How to Hack Someone’s iPhone
The iPhone is famous for the security and privacy of its users. With regular updates and the closed ecosystem of iOS, it’s pretty uncommon to hack into an iPhone. But if you’re wondering about the possibility of spying on an iPhone, then the answer is yes. There’re multiple ways you can access the other person’s iPhone without them knowing.
Let’s discuss how to hack someone’s iPhone remotely;
- Using spy apps
- Making use of phishing technique
- Taking help from the Find my iPhone application
- Using iCloud backup
- Employing advanced hacking methods
- Hiring a professional hacker

You might be thinking about how these methods work, don’t fret! We have tested and researched everything for you beforehand. Without further ado, let’s delve into them.
How to Hack Someone’s iPhone Without Access to it? Try mSpy!
mSpy isn’t a hacking application, but with its powerful capabilities, it can monitor every activity of the concerned mobile device. mSpy doesn’t have any requirements to jailbreak the iPhone. Using this app, you can;
- Track all text messages, even the deleted ones
- Monitor the GPS location of the iPhone user
- Access social media accounts, including Facebook, Instagram, Twitter, etc
- See the call record/history of the target user
- Get notification of particular trigger words whenever entered/received on the device.
And much more!
Let’s talk about how to hack someone’s iPhone remotely using mSpy:
Unlike other tracking applications, mSpy doesn’t bind you to install applications on the target iPhone. It only asks for iCloud credentials to give you access to pretty much everything on the concerned phone.
- Start with creating a free account through the official website of mSpy using your own password and email ID.
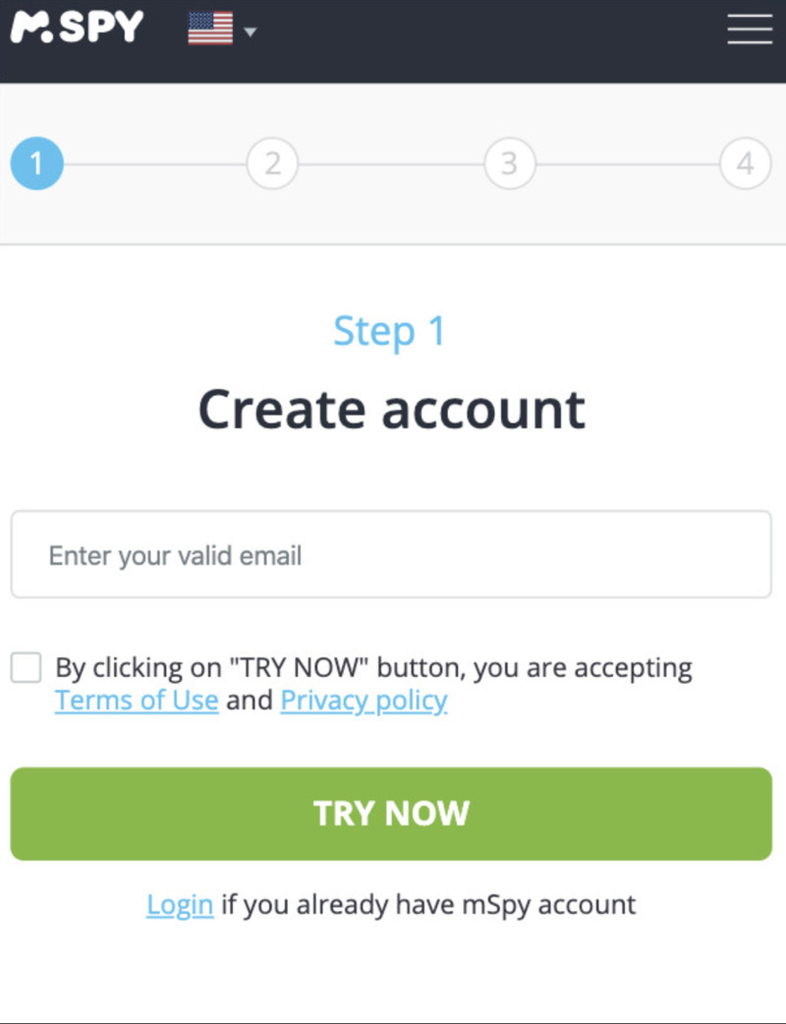
- Hit the ‘try Now’ button and select ‘OS’ on the next window
- Now, pick the desired subscription plan according to your particular needs
- Head over to your email inbox to receive the login credentials sent by mSpy
- Login into the application and insert iCloud details of the target user
Note: The two-factor authentication must be disabled on the required device
- Finalize the process and visit the mSpy’s dashboard to access all the activities of the victim’s iPhone

For the first time, it might take a little for mSpy to collect and deliver all the information. So, be patient!
Pros
- Offers a reliable multi-language customer support
- No requirement to jailbreak the device
- Works well with all versions of iOS
- No need to physically access the device
Cons
- Lacks backup functionality to retrieve wiped data
- One subscription is only valid for a single device
How to Hack Someone’s iPhone Password using Keylogger?
Keylogger applications are designed to track every stroke on the victim’s device. mSpy keystroke logger does the job exceptionally well by capturing everything on the target mobile phone. If you successfully install it onto someone’s iPhone device, you can easily record their passwords and later use them the way you want.
With mSpy keylogger, you can track;
- All types of messages, even the deleted ones— after app installation
- Notes, remainders, and even emails
- Every type of password entered
And many more.
Let’s discuss how to hack someone’s iPhone text messages and other details with this application;
- Visit mSpy’s official website and pick the subscription package best meets your particular needs.
- Enter your email address to receive all the guidelines over there
- Now, simply download the application on the victim’s iPhone
- On successful installation, head over to the dashboard of mSpy to see all the captured data in real-time
Pros
- Simple and quick procedure
- Gives you access to a big chunk of victim’s data
Cons
- You need the iCloud credentials of the target user
How to Hack Someone’s iPhone Password using Find my iPhone?
This Apple-designed application was originally meant to track lost or stolen devices. But, you can use it to hack someone’s passcode. The main purpose of the process is to unlock the mobile phone. This process involves a factory reset which would wipe away all the available data on the concerned iPhone. So, this method won’t give you direct access to other person’s data, but you can unlock the mobile phone to use it the way you want.
There are a few prerequisites for employing this method to hack a phone. Firstly, this feature should be active on the target device. In addition, iCloud credentials are a must to proceed with this process.
If you have both these things, then let’s get straight into hacking someone’s iPhone;
- Head over to the Find my iPhone application on your own mobile. If you don’t own an iPhone, then visit iCloud’s official website
- Log in with the iCloud credentials of the target user
- Now, select the required iPhone device you want to unlock to see its real-time location
- Hit the ‘Actions’ button below and select ‘Erase iPhone’
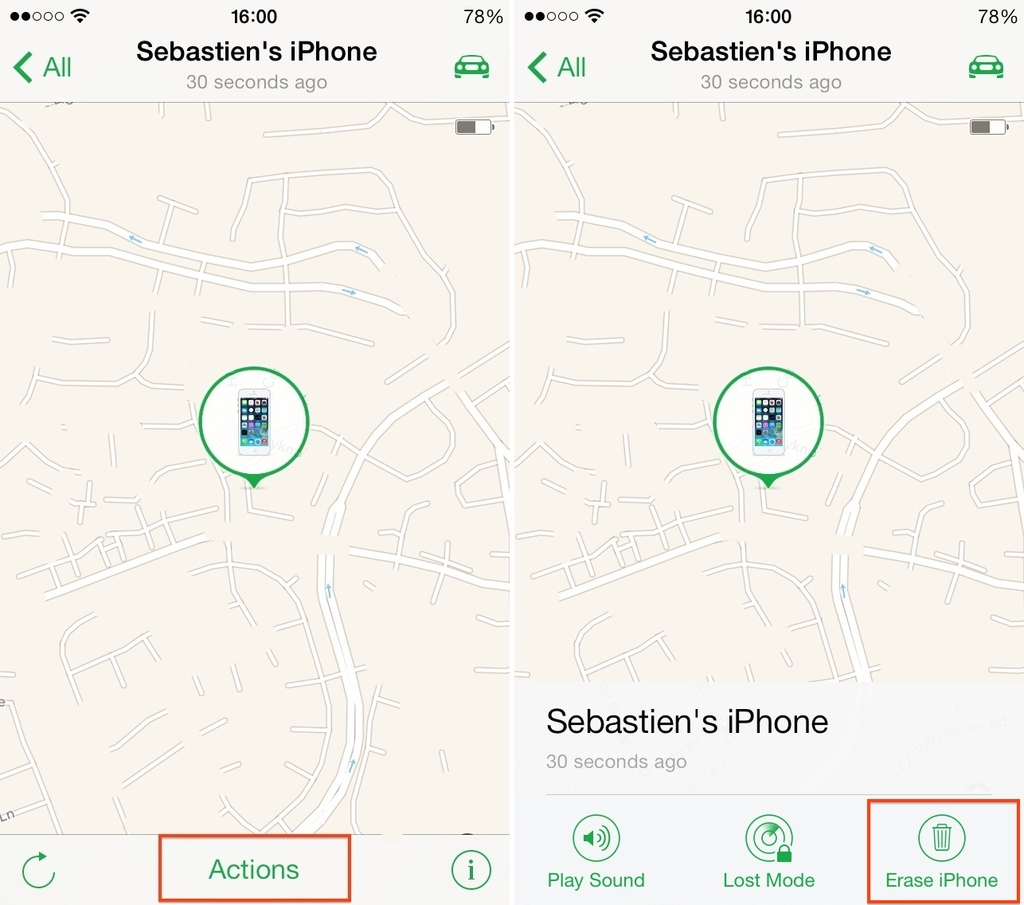
- After tapping ‘Confirm,’ it won’t take long to factory reset the device.
Now, you’ve unlocked the phone, use it the way you want!
Pros
- Simply and quick process
- No technical knowledge required
- No need to install any third-party application
Cons
- Highly risky as the target person will easily detect a factory reset phone
- iCloud credentials are needed to perform this method
- Find my iPhone services must be active on the target device
How to Hack Someone’s Phone without Touching it using iCloud Backup?
With the help of Apple ID, you can remotely access data on the target device. For this, you just need Apple ID details and a surety of disabled two-factor authentication. If two-factor authentication is active, then you need to physically access the concerned iPhone to steal the confirmation code.
If done successfully, you’d be able to view;
- Contact details of the target user
- History of outgoing & incoming calls
- All files in the iCloud Drive, including photos and videos
- Live location of the mobile phone
- iMessages details available on the device
Let’s discuss how to remotely hack an iPhone;
- Take any device and login into iCloud using the credentials of the target user
- Snoop around to look recently created iCloud backup on the concerned device
- If found, simply restore it
Now, you can access all the aforementioned data.
How to Hack an iPhone using Phishing?
Phishing is one of the most common techniques to perform any type of hacking. It is basically deceiving the phone owner to click on a link and enter their credentials. For instance, if someone receives an email or text from a bank or a government agency to provide them with basic information. Most people usually fall into the trap and provide all their details right away.
You need to exactly replicate the same. Just select any credible source, let’s say Paypal.
- Build a phishing website giving it the exact same look as the official website of Paypal.
Note: Be aware of grammatical errors, as a single mistake can spoil your whole effort. Use the official logo of the source to add a factor of credibility. The website domain name should closely match the official one like Paypaal.com etc.
- Once your website is ready, now create an email or text message with some sort of warning and add a factor of urgency. For instance, “someone tried to log in to your account, an urgent action is required.” You can even compel them by asking for confirmation of contact information.
- Make sure to add a link to your previously created website to this email or message.
As soon as the victim opens the link and enters his credentials, your website will save them for you. You have done it; just use these details to log in to their account whenever you want. Your phishing email might land in the spam folder of the victim, that’s why sending text messages are always recommended.
You can also try this trick on someone who frequently uses public WIFI. Just act as a middleman and push the person to enter credentials before accessing the WIFI connection.
Pros
- You can hack any type of account (bank, social media, etc.)
- You don’t need to access the concerned device physically
Cons
- Low success rate
- Requires investment in building a website
- Technical expertise is a requisite for this method
Use SS7 Vulnerability to Hack Someone’s iPhone
Common channel signaling system No.7 is a network communication protocol employed worldwide. It’s been in use since the mid-1970s and hasn’t been updated yet in any significant way. Due to outdated technology, hackers exploit its vulnerabilities to spy on required individuals.
These attacks try to exploit the authentication capability of communication protocols going over the SS7. If done successfully, hackers can access;
- Concerned device location
- Conversions over phone calls
- Text Messages and many more
If you’re a coding expert, then with just two things, you can hack someone’s iPhone without them knowing. These include;
- SS7 SDK
- A system operating Linux
Both of these things are easily accessible to everyone.
Pros
- The hacking toolkit is easily accessible
- A reliable method if you have the expertise
Cons
- High-end technical expertise is mandatory
- Risky procedure
How to Hack Someone’s iPhone Using Kali Linux?
Kali Linux is a famous programming language. This is mainly used for penetration testing or digital forensics of all devices, including iPhones. With the help of Kali Linux, you can spy on call logs, messages, and a lot of other important data.
Basically, the Android OS system is based on the Linux Kernel, which manages memory, controls drivers, and maintains the security of the device. This allows Kali Linux written codes to get desired access. If you have technical expertise, the same process can be replicated for an iPhone.
Pros
- Works with all types of devices and OS
Cons
- Advanced technical expertise is required
Hire a Professional Hacker to Hack into Someone’s Phone Remotely
If none of the above-mentioned methods works, then hiring a professional can be a desperate remedy. With advanced hacking skills, a well-equipped hacker can access any iPhone remotely.
For this, you need to find and hire a professional hacker, which isn’t an easy task.
Disclaimer: Such people are usually available over the Dark Web and other places of such kind, which aren’t appropriate for most users. You may lose all your money and become a victim of hacking. That’s why we don’t recommend this method.
Wrap Up
Now, you know all the methods commonly used to hack iPhones, along with their downsides. If you don’t have technical expertise, then we highly recommend using mSpy applications that are backed by the trust of millions of satisfied customers.
mSpy’s high success rate with the easy-to-use interface is a perfect blend for beginners and non-tech users. Give it a shot now!
No one has left a comment yet, be the first