How to Hack Someone’s Phone Remotely
With every passing day, more and more people are searching for how to hack someone’s phone remotely. Parents want to keep an eye on their children, and employers want to track the activities of their worker’s phones. Whatever the need, most people struggle to find an authentic way of hacking someone’s mobile device.
Even the majority of internet users find themselves in ambiguity about the possibility of hacking, whether spying on a phone is possible or not.
Let’s delve into the discussion.
Can You Hack Into Someone’s Phone Remotely?
Yes, it is possible to hack into someone’s phone without physical access to it. Here are a few widely discussed methods to hack someone’s smartphone:
- Using spy applications
- Employing keyloggers
- Trying phishing techniques
- Hacking with phone number
- Relying on advanced hacking methods

Let’s discuss each of these methods to find out how to hack someone’s phone remotely.
Disclaimer: This write-up is just for educational purposes. Some of these methods might be illegal in your country. Before trying any of these techniques, make sure you’re fully aware of your country’s laws.
How to Hack into Someone’s Phone Remotely? Try Cocospy!
You can use the Cocospy application to access any mobile device, irrespective of its operating system. On top of that, you can sneak on almost everything available on the target device, including;
- Tracking of phone calls, SMS, and location details
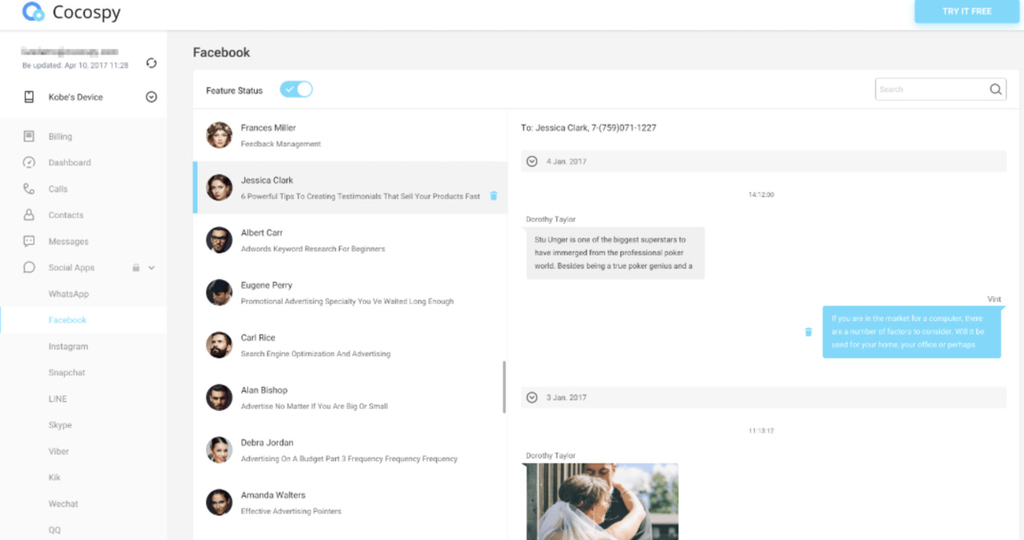
- Spying on almost all social media applications, i.e., WhatsApp, Facebook, Twitter, etc
- Providing geofencing alerts —rarely available in spying apps
- Checking contact details and providing conversation timestamps
- Identifying sim location of the target user
- Viewing network career details, IMEI, carrier
And the list goes on!
This spying process can be bifurcated into two portions: Android and iOS. Let’s discuss how you can do it with Cocospy;
How to Hack Someone’s Android Phone Remotely with Cocospy?
While using this app, there is no requirement to root your Android device. Additionally, it performs most of the operations remotely after one-time access.
Note: All spy applications require one-time access to the mobile phone of the target user, and so does the Cocospy.
Please note that Cocospy is a spy application but has the potential to fulfill all of your hacking needs. Let’s discuss the step-by-step guide on how to hack someone’s Android phone remotely;
- Head over to the official website of Cocospy and click on sign up
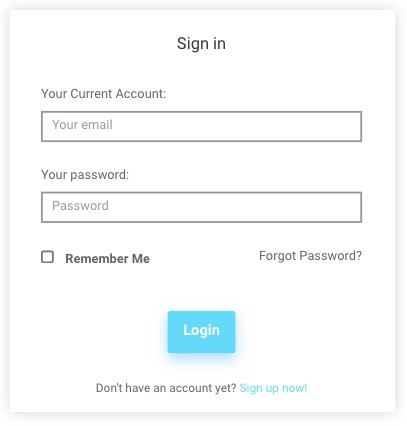
- Enter your legitimate email address and create a password
- This will lead you to the subscription page, where you can pick the best pricing package according to your preferences
- A new window will open where you’ll give any desired name to the device of the concerned person. Make sure to opt for the operating system “Android”
- Now it’s time to install Cocospy on the other person’s mobile
- For doing that, permit unknown sources to install applications on the device. Head over to the phone’s setting, open security, and find & enable unknown sources
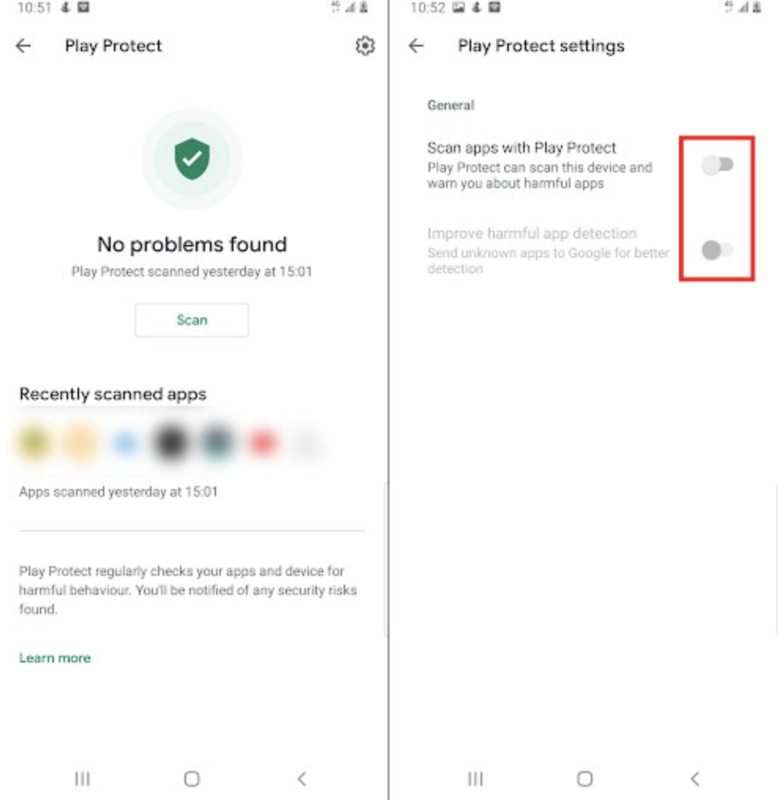
- Now go to the Google option from the settings and click on security. Finally, disable both “Scan device for security threats” and “Improve harmful app detection.”
- Just go to any browser and type in “trackpro.vip” and hit enter to download the Cocospy. Follow on-screen instructions to download & install the application on the target user’s device.
- Open the app and agree to the terms and conditions after reading them.
- Finally, enter the email and password that we kept in the initial steps
- Once again, proceed with on-screen procedures to finish the setup on the other person’s device
Note: Make sure to give all the required permissions and usage access
- Once done, simply select ‘hide the application’ to turn on the stealth mode. You can always evoke the applications by typing **001** in the dialer.
- Finally, go back to your PC and access Cocospy’s dashboard, and start monitoring the activities of the concerned person.
How to Hack Someone’s iPhone Remotely with Cocospy?
Cocospy works best on iPhones without any additional requirement of jailbreaking the target device. In addition, you don’t even need to physically touch the target user’s smartphone.
You only require access to iCloud credentials active on the iPhone of the concerned user. By using this information, Cocospy builds a clone of their mobile phone. After that, you can easily monitor all their activities from the dashboard.
Let’s discuss how remote hack for iPhone works;
- Create the free account and decide on the subscription package according to your need
- Select the device and operating system of the target user’s iPhone
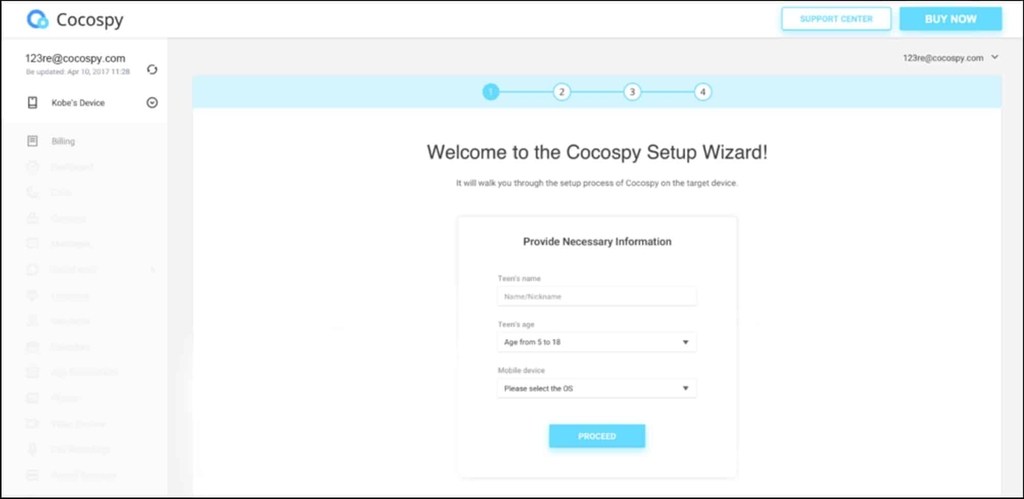
- Now use the iCloud credentials of the required person to login into the application.
Note: Please, make sure two-factor authentication is turned off and iCloud backup is enabled
It might take a little for the application to synchronize all the data.
- Once done, hit the finish button to complete the process.
- Finally, visit Cocospy’s dashboard to remotely monitor all activity of the required person
Pros
- No requirement to root/jailbreak the device
- High accuracy with real-time sync of data
- Easy to install and use
- Compatibility with both iOS and Android
- Complete remote operation on iOS device
Cons
- Requires iCloud details for iOS monitoring
- Some advanced features demand rooting/jailbreaking the target device
How to Hack Someone’s Phone Remotely using a Keylogger? Try Cocospy keylogger
A keylogger mainly tracks and shares every stroke the target person makes on their cell phone. With a reliable keylogger like Cocospy, you can spy on all the password entries made on the other person’s cell phone.
If installed and worked correctly, you will not only be able to hack someone’s phone remotely, but you can also spy on all of their social messaging applications.
To install the Cocospy keylogger, one-time access to the concerned mobile phone is mandatory.
- Avail the subscription of Cocospy keylogger according to your need
- Head over to install the application on the target user’s mobile phone
That’s it. Now, all of the password entries will appear in front of you, thus giving you uninterrupted access to another person’s accounts and devices.
Pros
- No requirement for technical knowledge or programming skills
- Easy to install and operate
- Works in the background without notifying the victim
Cons
- Only paid versions of these keyloggers are effective
- Physical access to the target person’s phone is required
How to Hack Someone’s Phone Remotely for Free? Try Phishing!
Phishing is one of the widely used techniques to hack someone’s phone without touching it.
The primary principle behind this method is to compel the target user to open up your link and enter their credentials. You can send a link either via email or text message.
You might be wondering, who would be that foolish to enter their details on something suspicious? Yes, you’re thinking right, but we create a replica of credible sources with phishing. So, they don’t figure out the intentions behind the trick.
Don’t fret; let’s get straight into it and discuss how to hack someone’s phone without touching it for free.
- Select a credible source like a government institution —National Security Department— or a banking channel —like Payoneer— to impersonate. Let’s take Payoneer for the sake of an example.
- Develop a website looking for an exact copy of Payoneer’s official website. Make sure to grab the domain and email similar to the main source— for instance, payoneeer.com, thepayoneer.com, etc.
- Now, craft the exact message to be delivered to the target user via an email or SMS. If you add a factor of seriousness and urgency, then the success rate can be increased. For instance, write something like, ‘someone tried to login into your account; an urgent action is required.’
Note: if you’re trying to hack someone’s social media accounts, then try to replicate the exact email text that the social platform sends itself. It will increase the chances of success.
- Don’t forget to incorporate the official logo of the Payoneer to add a factor of credibility.
- Now, just send that email or message to the target person
That’s it. Wait until the victim receives the email/text and clicks on the link to add the relevant details. If they did, you’d receive the account credentials of that person. Just use them to hack the cell phone remotely.
Pro Tip: Your email may end up in the spam folder, so always prioritize sending the link via SMS.
Pros
- No need to physically access the concerned cell phone
Cons
- Relatively low success rate
- Requires basic technical skills
How to Hack Someone’s Phone without them Knowing using Advanced Hacking Methods
Advanced hacking methods can be effective in hacking Android and iPhone smartphones, but as the name suggests, these aren’t beginner friendly. Coding knowledge is the primary prerequisite of these processes.
Here are a few commonly known advanced hacking methods to remotely hack someone’s phone;
- Try IMSI catcher or stingray mobile phone hack
- Employ RAID method
- Perform a control message attack
- Make use of SS7 vulnerability
- Use cloak and dagger attack
- Hire a professional hacker
Let’s discuss each of them along with their pros and cons to find out how to hack someone’s phone successfully.
How to Hack a Mobile Phone using IMSI Catcher or Stingray
Before going into details, let’s first understand how mobile networks operate. Smartphones use IMSI numbers to identify and connect to nearby cellular towers. If by any means you become successful in intercepting the frequency, the cell phone details of the other person can be tracked down. This is the exact working principle of this method.
You just need to introduce ‘fake cell towers,’ ‘cell-site simulator,’ commonly known as Stingray.
The matched frequency cell phones in the area will now connect to this fake tower, leaving them vulnerable to hacking attacks.
To hack someone’s phone remotely with this method, you need;
- Get an SDR—software-defined radio
- Now, give some automated instructions to SDR for connecting to cell phones— you can get these codes from Github for free.
- Install Ubuntu and download the IMSI Catcher script
- Install a program that can facilitate frequency management. This helps in finding the frequency of the scan
- Keep it changing until SDR catches some frequency
- After catching a frequency, IMSIs will start appearing on your screen instantly.
This is how you can use IMSI Catcher or Stingray to hack someone’s phone remotely.
Pros
- No requirement for physical access to the cell phone
- Relatively cheaper than other advanced hacking methods
Cons
- Technical knowledge of coding is mandatory
- Accurate frequency match-up isn’t easy
- Low success rate
How to Hack Into Someone’s Phone Using the Midnight Raid Method?
If you want to hack someone’s phone without them knowing, then the Midnight Raid method is meant for you. Just like every other advanced hacking method, this isn’t a beginner-friendly method. But, some level of basic understanding can ease the hassle for you.
The best thing about the Midnight Raid method is that it doesn’t need any complex hacking equipment. To spy on someone’s cell phone, you need:
- Two mobile phones. Among them:
– One will act as a GMS modem for the laptop
– The other will serve to receive the information - A WIFI compatible laptop
- A data-retrieving tool
- And a WAP push-up application
Now that you have all these tools ready, let’s start the hacking process;
- Go near the concerned mobile phone— this is usually performed when the victim is away from his cell phone or asleep; that’s why we call it the “Midnight Raid.’
- Create a message like, ‘Your Phone has been Hacked,’ and send it to the required person’s phone
- Now, use the WAP push-up application to create a push message that will appear on the target user’s mobile screen, alerting him to install the ‘security software.’
- The concerned person doesn’t need to click the link, instead push message would be designed in a way to automatically run the browser application.
- That’s it; now, the data-retrieving tool will collect and update you with the mobile phone’s unique ID, generally known as the IMSI number.
Using this method, you can also collect other vital information on the target person’s mobile phone, such as contacts.
Pros
- It doesn’t need a high-end hacking kit
Cons
- Low success rate
- Requirement of basic technical knowledge
- Give access to limited data in a single go
How to Hack Phones Remotely with Control Message Attack?
The control message attack method is pretty complex for beginners but effective in yielding results. This process involves sending a control message to the target user’s device.
This message moves forward through the Global System for Mobile Communication, commonly known as GSM. Finally, it reaches the other end— the victim’s phone— which should be connected to the WIFI network to make it successful.
In order to hack someone’s phone, simply uncheck SSL or sniff internet traffic with the help of a hacking toolkit. These steps leave the target user’s device vulnerable to attacks.
Pros
- A quick method to hack phones
Cons
- Relatively complex process of hacking
- Requires technical expertise and proper understanding of tools and codes
- It doesn’t generate results in most cases
How to Hack a Smartphone for Free using SS7 Mobile Tracking?
SS7 (Common Channel Signaling System No.7) is the leading protocol specified for establishing network communication globally. Intelligence companies and mobile operators mainly use it. But you can also leverage this old network communication setup to hack someone’s phone remotely.
You only need two things along with expertise in this process;
- A system operating Linux
- SS7 SDK
Luckily, both of these things are easily available on the internet. With the help of this method, you can intercept messages, calls, and location histories of the victim.
So, if you’re concerned about eavesdropping on calls and other people’s private conversations, then vulnerabilities in the SS7 system can help you a lot.
Pros
- Relatively high success rate
- Quick process
Cons
- Risky procedure
- Only technical experts can make use of this method
This is how you can hack into someone’s phone remotely to see text messages and other details.
How to Hack any Android Phone Remotely Using Cloak and Dagger Method?
In order to hack any phone remotely, you can exploit two key permissions of Android devices;
- Cloak: System Alert Window
- Dagger: Bind Accessibility Service
For any app installed from Google Playstore, if it requests ‘system-alert-permission’ in its file AndroidManifest.xml, the system immediately provides the permissions. This is where the ‘cloak’ part of hacking starts.
Hackers mainly take advantage of this permission to trap users to cover their UI. Then tricks them into clicking on activities below the overlay.
Once the accessibility setting is enabled, most of the user’s information, including lock screen key presses, keystrokes, and multiple other things, can be traced.
So, if you’re wondering about how to hack someone’s Android phone remotely, then the cloak and dagger method is the answer.
Pros
- Currently, there’s no proper method to debunk this process
- Provides you with the lock screen details of the victim
Cons
- This process is highly technical, so coding expertise is a must
- Only workable for Android devices
Hire a Professional Hacker to Hack Someone’s Phone
If none of the above methods are approachable for you, then hiring a professional person can be your last resort. There are multiple marketplaces to find talented hackers to carry out various activities. In order to hack into a phone remotely, you need an expert person in this particular category.
You can find people from places like the Dark Web, but be cautious while visiting such places.
Disclaimer: It’s really hard to find a credible hacker to access someone else’s mobile phone. There are wide chances that you might end up hacked by these people and even lose all of your money. That’s why only opt for this method when none other works, and hacking another person’s mobile phone is inevitable; otherwise, avoid it at all costs.
Wrap Up
Now you know a multitude of methods about how to hack into someone’s phone without touching it.
Among all, Cocospy is one of the most reliable options ensuring a higher success rate. So, if you’re interested in hacking into someone’s phone, then spending a few dimes on Cocospy is the most recommended option!
Give it a shot now!
No one has left a comment yet, be the first